BlackHat MEA CTF 2022 — Forensic Challenges

The challenge, titled “Mem,” was part of the Forensics section. We were given an archive that contained a raw memory image, along with a short description of the task — and here’s basically my approach to solving it during BlackHat MEA CTF 2022.
I honestly found this challenge super engaging because of how tricky it was, and I kinda wanted to share my experience since at that time I was still a complete noob just starting my CTF journey.
So yeah, we had this raw memory image that was captured before the PC shutdown, and the goal was to do some memory forensics analysis on it.
Volatility

Volatility is this really powerful memory forensics framework written in Python under the GNU GPL. Basically, it lets you extract digital artifacts from RAM without touching the original system. It works completely independent of the machine being analyzed but still gives you visibility into its runtime state. It’s designed to help people understand the techniques (and the headaches 😅) that come with analyzing memory images, while also being a solid base for more research in the field.
Solution
I jumped straight into the raw image. The first step was to grab some basic info about it:
1 | python2 /usr/bin/vol.py -f mem.raw imageinfo |
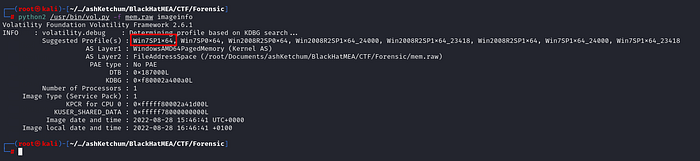
The imageinfo output tells you which profile to use with the --profile=PROFILE flag when running other plugins. Sometimes it’ll suggest more than one profile if they’re closely related. It also prints the address of the KDBG structure (_KDDEBUGGER_DATA64), which is what plugins like pslist and modules rely on to grab the process and module list heads.
So from here, we know the profile is Win7SP1x64. That means we can start exploring with pslist, psscan, and so on.
What is pslist?
The pslist plugin lists processes by walking the doubly-linked list pointed to by PsActiveProcessHead. You get details like the offset, process name, PID, parent PID, thread count, handles, start/exit times, and since 2.1 even session ID + Wow64 info.
What is psscan?
The psscan plugin instead uses pool tag scanning to find processes. This way, you can also detect processes that have been terminated or hidden by rootkits. Downside is — if a rootkit overwrites the pool tags, psscan won’t help (though that’s rare in practice).
1 | python2 /usr/bin/vol.py -f mem.raw --profile=Win7SP1x64 pslist |
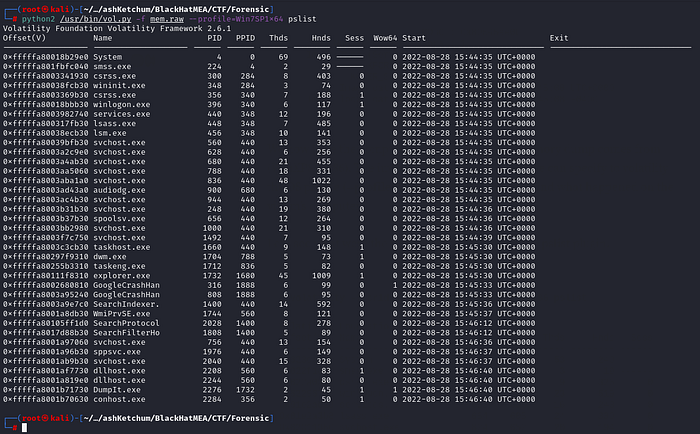
Nothing suspicious jumped out here, so I switched gears and started looking for file objects in memory — thinking maybe the flag was in some file that was opened at the time. For that, I used filescan.
What is filescan?
The filescan plugin looks for FILE_OBJECTs in physical memory using pool tag scanning. It’ll show files that are still open even if a rootkit is hiding them on disk. The output includes the file offset, filename, number of pointers/handles, and effective permissions.
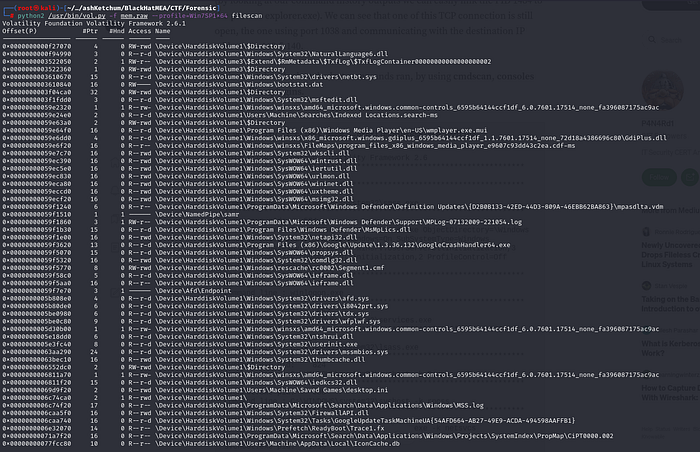
Since the output was huge, I just grepped for keywords like ctf and flag:
1 | python2 /usr/bin/vol.py -f mem.raw --profile=Win7SP1x64 filescan | grep ctf |
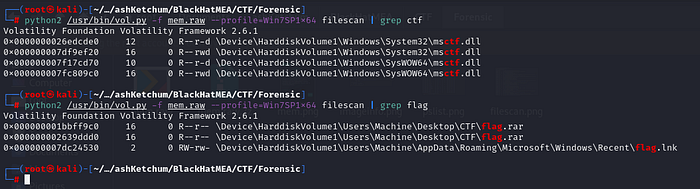
Boom — there it was: a file called flag.rar. Looked like our target.
So I dumped it out using:
1 | python2 /usr/bin/vol.py -f mem.raw --profile=Win7SP1x64 dumpfiles -Q 0x000000001bbff9c0 -D /your/path/to/save/file |
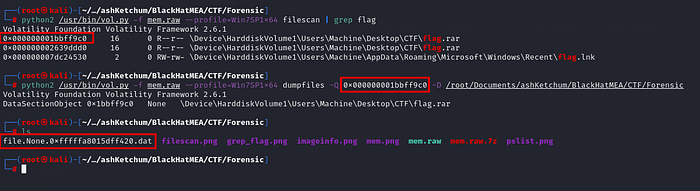
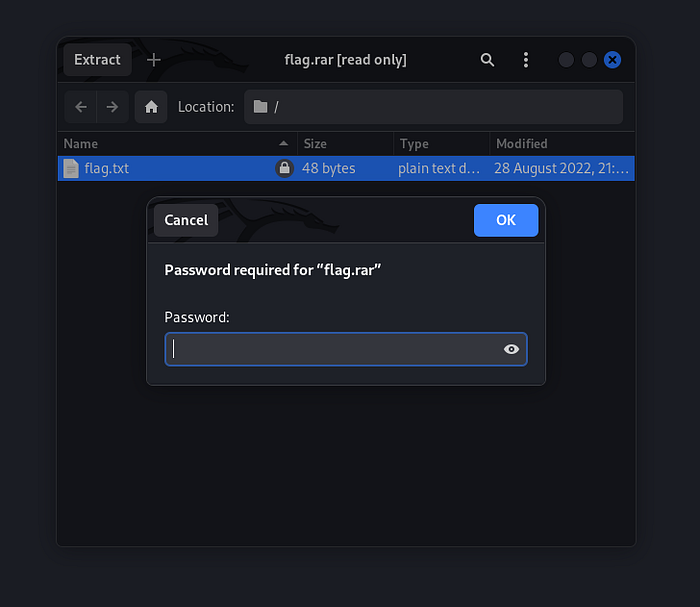
But when I opened the rar file… yep, password protected 😑 So I had to dig a bit deeper.
My first guess (and it turned out to be right) was that the password could be hanging around in environment variables. So I ran envars. This plugin shows all kinds of things: CPU info, architecture, process current directory, temp dir, computer/user names, and other juicy artifacts.
1 | python2 /usr/bin/vol.py -f mem.raw --profile=Win7SP1x64 envars |
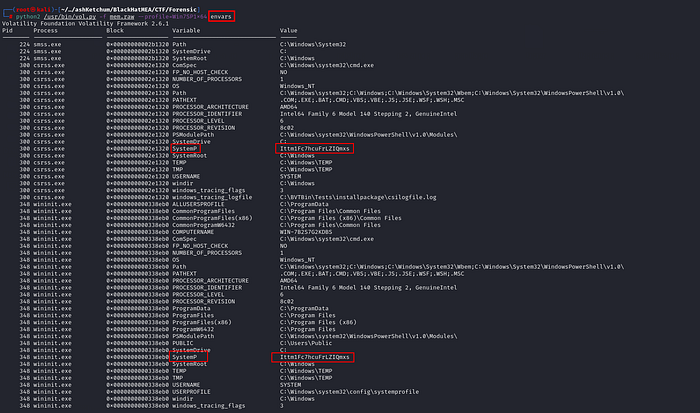
Sure enough, I found a variable called SystemP with a strange value: Ittm1Fc7hcuFrLZIQmxs. Looked totally random, so I figured it was the password — and yep 🤭 nailed it.
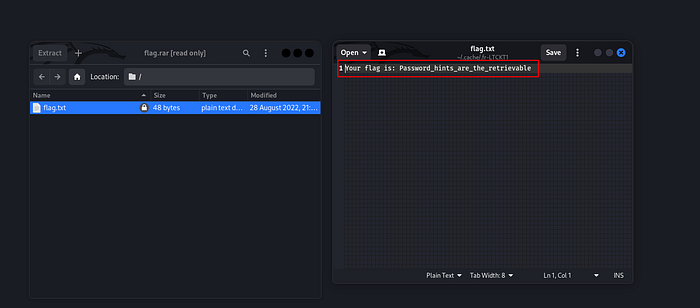
1 | flag = BlackHatMEA{Password_hints_are_the_retrievable} |
So yeah, that was the flag 🎉
We actually qualified for the BlackHat MEA 2022 Finals, but sadly we couldn’t make it to Riyadh 😓

- Title: BlackHat MEA CTF 2022 — Forensic Challenges
- Author: Depe
- Created at : 2025-08-21 11:26:15
- Updated at : 2025-09-02 04:12:47
- Link: https://depe.blog/2025/08/21/BlackHat-MEA-CTF-2022-—-Forensic-challenges/
- License: This work is licensed under CC BY-NC-SA 4.0.